Security Analysis provides a foundation for all forms of planning, preparedness, and security in the face of threats to our well-being. It calls for a hard and disciplined look at our surroundings, which helps us to anticipate threats, recognize them when they appear, and prepare in advance to manage or defeat them.
Security Analysis has several components, each addressed in detail in following articles in this series. They are best undertaken in the order shown:
- A Threat Assessment lists and evaluates real and potential, violent and non-violent threats to our well-being. It's an exercise in deductive analysis, based on facts and trends.
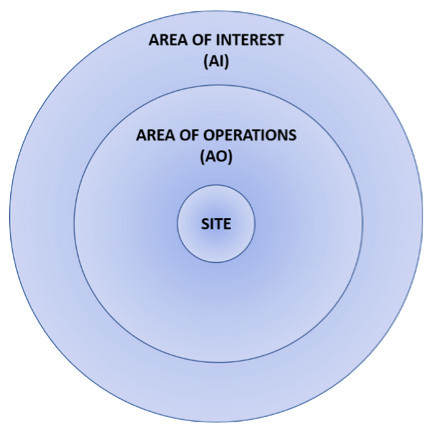
- A Site Survey characterizes a defined location, the target we hope to protect, which could be a home, neighborhood, business, church, school, or community. The survey describes in detail all elements that can affect the site's security, such as boundaries, access and egress routes, physical security, and human elements such as the numbers, types, abilities and activities of occupants, and existing security and emergency plans and preparations.
- An Area Study looks at a broader surrounding area, and at conditions generally beyond our control or direct influence, such as terrain, climate, population numbers and density, economics, politics, infrastructure, and social cohesion. That city an hour's drive away, for instance, can have a profound effect on our security in both normal and off-normal conditions.
- Vulnerability Assessment is the final step in a Security Analysis, based on information developed in all the earlier stages, comparing our prioritized threats against the target characterized by our Site Survey and Area Study. It identifies strengths and weaknesses in our current posture, and helps us identify upgrades worth pursuing.
Security Analysis is an iterative process; it is never complete and must be re-addressed and updated as conditions change. The greater effort is expended on the first pass through, providing a detailed and organized body of information and analysis that can be reviewed and amended as necessary.
If can be a lot of work for an individual, and indeed the best and most honest product requires a team effort to bring different perspectives and experience to bear. But it is worth the investment. Without it, the potential for wasted time, money, and effort addressing security concerns is enormous. There are many threats to our well-being, and it is easy to put our heads in the sand and ignore them, or focus on only a few that for one reason or another seem significant, or give too much credit to measures that have been adequate in the past. That can result in being blindsided by threats we ignored or discounted, with potentially terrible consequences that might have been averted by a more disciplined and objective approach.
Confidence in our preparations against one or a family of threats should not lead to complacency. For instance, we may live in a quiet rural or small-town community with low property crime rates, where "nothing ever happens" beyond misdemeanor vandalism and mischief – until meth labs or drug trafficking organizations get a foothold, or spill over from nearby transportation routes and markets. Shortages and supply chain disruptions may not have a major effect on our daily life – until they do. Political violence may be something we see on TV or the Internet, in far off urban centers, until it arises in our community or metastasizes from its point of origin.
The Security Analysis processes outlined in this series have been distilled and adapted from methods proven in the fields of risk management, intelligence, and security for many years. They are scaled for smaller civilian applications, with a less quantitative approach. Feel free to abbreviate or modify them further to make a better fit for your circumstances and concerns, but don't do it for convenience alone, or to protect your biases or predetermined notions.